D4 software stack - new version released
Following the Programming Methodology Framework aka PMF we choose to release D4 software component early, and often. All interested parties are invited to install and use these, and to report bugs on their respective Github repositories for further improvements.
New Versions
D4-core bumped
D4-core server and client are bumped to version 0.3 and D4-goclient to version 0.2.
- D4-core server:
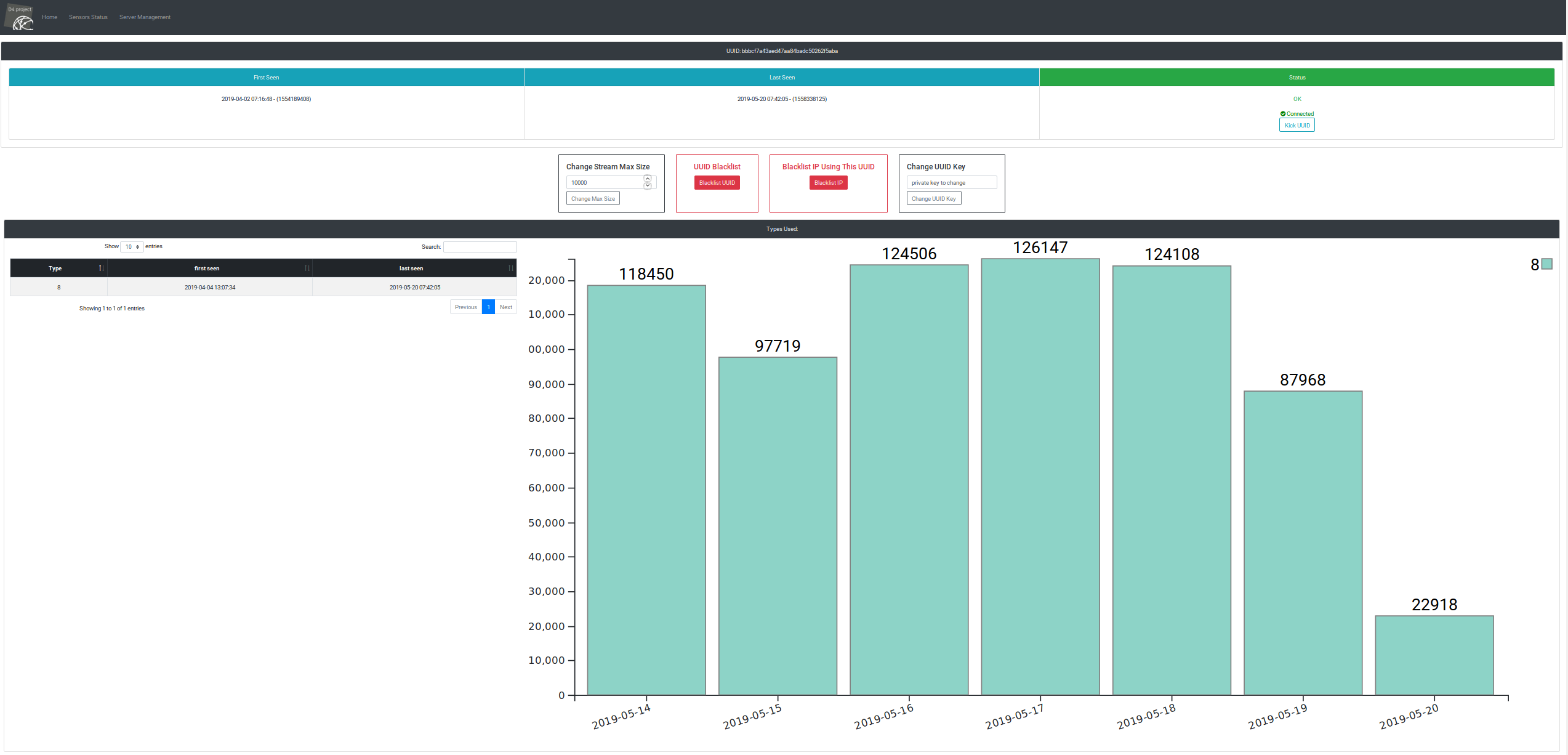
- new kick functionality to remove sensor per UUID
- extended types is now supported by the D4 server (see Meta-Headers in architecture)
- many bugs fixed (following intensive use of existing new sensor such as Passive DNS and Passive SSL)
- statistics per sensor added to the UI
- various improvements including save JSON to disk and others depending of the type
- D4-core client:
- improvement to compile on older version of Linux + OpenBSD
- D4-goclient:
- support for extended types (type 254)
- DNS resolution
- multiple bugs were fixed
IPASN-History 1.0
- support for BGP dumps
- load RIPE dumps announces in addition to CAIDA
BGP Ranking 1.0
- port of BGP Ranking to python 3.6
- ARDB back-end
New Software
analyzer-d4-pibs
Reads pcap files and identify potential DDOS related traffic such as backscatter.
- consumes pcap files, identifies potential backscatter and displays it on standard output
- writes potential DDOS traffic in pcap file
sensor-d4-tls-fingerprinting 0.1
Extracts TLS certificates from pcap files or network interfaces, fingerprints TLS client/server interactions.
- extracts TLS certificates from pcap files or network interfaces
- fingerprints TLS client/server interactions with ja3/ja3s
- fingerprints TLS interactions with TLSH fuzzy hashing
- writes certificates in a folder
- exports in JSON to files, or stdout
analyzer-d4-passivessl 0.1
Fetches TLS sessions generated by sensor-d4-tls-fingerprinting and massage the dataset to be usable by the forseen passivessl webservice.
- creates a Postgresql database that stores data about TLS sessions, certificates (and chains of certificates), public keys, and related fuzzyhashes provided by sensor-d4-tls-fingerprinting
- fetches TLS sessions from a d4-core server redis queue
- fetches TLS sessions from a folder containing their json descriptions
- expose chains of certificates as an ltree
- provides Postgres function to query sessions by TLSH fuzzy hash / threshold
d4-server-packer 0.1
Packs up d4-core server Virtual Machines.
- sets up a ready to use d4-core server
- packs up an Open Virtual Appliance for Virtual Box
